|
Click the comments link on any
story to see comments or add your own.
Subscribe to this blog

RSS feed
|
Home
04 Dec 2009
In a recent discussion among mail system managers, we learned that one
of the large spam filter providers now has an option to reject all mail
from ESPs (e-mail service providers, outsourced bulk mailers) regardless
of opt-in, opt-out, spam complaints, or anything else, just block it
all. Some of the ESPs wondered what would drive people to do that.
We are bombarded by ads from the moment we get up until the moment we go
to sleep. There's ads on the radio, ads on TV, ads in the newspaper, ads
on billboards, ads on the bus, ads on the fricking steps in the NYC
subway. In my physical mailbox, where I used to throw away about one
worthless little newspaper full of ads a week, now it's one or two a day.
The reality is that recipients do not care if they get the vast majority
of what ESPs send. Even if we might have at one point checked the box to
get Valuable Offers for More Fabulous Products Like This, now it's just
more stuff in the gusher of ads. If there's a button to push to make
their inboxes an ad-free zone, it really shouldn't come as a surprise that
people push it.
For the minority of stuff that people do want, like the daily
headlines from newspapers, or perhaps the weekly roundup of cheap
plane fares, there's better ways to get them than e-mail. An RSS or
Twitter feed is entirely under the recipient's control, meaning
that no sleazy marketing manager can try to shove his messages to the
top of My Yahoo, or to insert his feed if I didn't ask for it.
If I lose
interest and unsubscribe, it is gone instantly, permanently, and
reliably. If I were a mail manager, I would be delighted to push the
no-ESP button, then show a few of my users how to set up feeds for the
trickle of stuff they really want, because now the management burden
is on them, not on me.
For ESPs, if there is any argument whatsoever about whether recipients
want your mail, you lose. Yes, it's hard to read their minds and only
send them what they want, but thats how competent ESPs make the big
bucks.
(Several mail managers at very large ISPs wrote privately to thank me
for my note and wish they had that button, but they asked me not to
name them since ESPs are so excitable.)
Stable link is https://jl.ly/Email/jmis.html
03 Dec 2009
Three days ago I blogged about the credit card
purchase checks that Capital One sent me, that appear to be interest free
30 day loans, which means modest amounts of free money.
Today they sent me more checks.
See more ...
Stable link is https://jl.ly/Money/capone2.html
30 Nov 2009
Earlier this year, the New Zealand Department of Internal Affairs,
the US Federal Trade Commission, and the Australian CMA
broke up a large fake drug spam ring known as Herbal Kings,
run by New Zealander Lance Atkinson. The NZ government fined him NZ$108,000
(about US$80,000) which, while a substantial fine, seemed pretty small
compared to the amount of money he must have made.
But today, at the FTC's request a US judge fined Atkinson US$15.5 million,
and got his US accomplice Jody Smith to turn over $800,000, including
over $500,000 in an Israeli bank.
This is the largest spam fine I'm aware of, and the $500,000 is one of
the largest international recoveries.
Atkinson hasn't paid the $15M, but since he is in jail, it seems
reasonably likely that the various governments will be able to track down his
assets by the time he gets out.
Spammers are in it for the money, and to the extent they can keep what they
get, they'll keep spamming.
Fines that wipe out the profits, and in particular fines that can actually
be collected are essential if we're going to make any progress against spam.
Fortunately for the FTC, Herbal King's spam was sloppy, with faked headers
and broken opt-out links, which are among the few things that the weak
CAN SPAM law forbids. If the spammers had been more careful, the fake
drugs would still be illegal, but it would
have been harder to prosecute them in the US since CAN SPAM wouldn't have
applied.
You can read the
NZ release on the CAUCE web site
and the
FTC release
on the FTC's web site.
I assisted the NZ government as a technical expert, providing advice to
the court explaining how Atkinson's actions matched what the law forbids.
Stable link is https://jl.ly/Email/fifteenmil.html
I have a Capital One Visa card that I haven't used in a long time.
Every few months they send me cash advance checks, and I can see
their increasing desperation as the terms of the checks keep getting
better.
The usual deal is a 2% or 3% transaction fee when you write the check,
then they charge interest starting the day you write the check at a
rate which on my account would be 24.9%. These are such an awful
deal that rather than dropping them in the recycling bin at the post
office, I bring them home and shred them.
A few months ago they started sending checks offering no transaction
fees, which improved them them to merely undesirable, but a few weeks
ago they sent me a set with no fees and small print on the back of
the letter saying they "Are treated as purchases according to the terms
and amendments of your Customer Agreement." Hmmn.
See more ...
Stable link is https://jl.ly/Money/capone.html
19 Nov 2009
ICANN has opened their new fast track
process for "countries and territories that use languages based on
scripts other than Latin" to get domain names that identify the
country or territory in its own language.
It's not clear to me what the policy is supposed to be for countries
whose languages use extended Latin with accents and
other marks that aren't in the ASCII set.
Any country that uses an extended Latin character set can use extended
characters in 2LDs right now, and I can't offhand think of any whose
current unaccented two-letter ccTLD isn't an adequate mnemonic for
their name. But let's say that Serbia feels that .RS is kind of lame,
so they apply for and get .СÑбиÑа which is perfectly reasonable, since
that's the Cyrillic character set.
Then Romania decides that .RO is too generic, so they ask for .România
with the circumflex over the â, as it is properly spelled in Romanian.
That's an IDN, so how can they say no?
Hey, say the Hungarians, they got their country names, we want
.Magyar. Oh, no, that's ASCII, that will be $185,000 and a highly
uncertain multi-year process. Really?
Stable link is https://jl.ly/ICANN/nonlatin.html
09 Nov 2009
At its recent meeting in Seoul ICANN announced with great fanfare
that it's getting ever closer to adding lots of new Top Level
Domains (TLDs). Despite all the hype, as I have
argued before, new
TLDs will make little difference.
There are two mostly separate kinds of new TLDs. One is TLDs for
countries in non-ASCII character sets, known as IDNs. They're much
less controversial, and ICANN will soon issue at least a few
politically expedient ones like .ä¸å½ with the name in Chinese
which would be equivalent to .CN. This is the only real TLD problem,
it was waiting for technical specs and implementation (not from
ICANN), but that is now largely done.
The controversial issue is domains with random new names, gTLDs. I
agree with my old friend Lauren Weinstein that this is a tempest in a very
expensive teapot, because all of the purported reasons that people
want new TLDs have been proven false, and the one actual reason that
a new TLD would be valuable has no public benefit.
See more ...
Stable link is https://jl.ly/ICANN/teapot.html
08 Nov 2009
Banks love it when their customers do their transactions on line, since
it is so much cheaper than when they use a bank-provided ATM, a
phone call center, or, perish forbid, a live human teller.
Customers like it too, since bank web sites are usually open 24/7,
there's no line and no need to find a parking place.
Unfortunately, crooks like on line banking too, since it offers the
possibility of stealing lots of money.
How can banks make their on line transactions more secure?
See more ...
Stable link is https://jl.ly/Money/securetrans.html
25 Oct 2009
(Thanks to Chris Lewis for permission to adapt this)
Everyone who uses e-mail needs spam filtering, and some filters definitely
work better than others. Some people we know were trying to design tests
of filter quality, which turns out to be extremely difficult.
What one might call 'filtering quality'
assessment, should be the very very last step after
"does it have the features I want?", "does it install/is it
supported/supportable?", "does it crash?", "does it make lots of stupid
mistakes?", "is it likely going to compare favorably with what we already
have?".
You have to do the latter before the former. The latter is relatively easy.
The former is what people keep asking about, and is the really really hard
part to do right.
See more ...
Stable link is https://jl.ly/Email/filtertest.html
07 Oct 2009
A recent message in the Risks Digest called
Risks
of believing what you see on the WayBack Machine (archive.org)
claims that:
I have now encountered 2 legal cases in 3 months in which a plaintiff saw
images on the WayBack Machine (www.archive.org) and believed that they
indicated events in the past that never happened.
This is a big deal in legal circles, since archive.org is widely used
in court cases to show the state of a web site at a given time, which
can be critical in, for example, cases where the site shows prior art
for a patent or infringing copies of copyrighted material.
If the archive entries aren't reliable,
all of these cases are thrown into doubt.
Needless to say, it would be many defendants' dream come true if
courts were to stop accepting archived copies.
I have analyzed the material cited in the article and find that the
archive is fine, and his claims to the contrary are somewhere between
disengenuous and deliberately misleading. Here's why.
See more ...
Stable link is https://jl.ly/iarchive.html
21 Aug 2009
On Wednesday, Project Honey Pot
filed
an unusual
lawsuit against "John Does stealing money from
US businesses through unauthorized electronic transfers
made possible by computer viruses transmitted in spam."
Their attorney is Jon Praed of the
Internet Law Group,
who is one of the most experienced anti-spam lawyers around,
with whom I have worked in the past.
The goal of this suit is to identify the criminals behind a vast
amount of theft through the ACH, the Automated Clearing House that
handles direct deposits and electronic payments in the US. The
pattern is that the bad guys install malware on the PC of company
financial officers, and use it to make ACH transfers to money mules
who then wire it out of the country.
Although the primary target of this suit is the crooks, an equally
important subsidiary target is banks, who have consistently
stonewalled attempts to learn about the extent of the losses the
details of the scam, and what the banks are doing to deter it.
Bank stonewalling is not a new problem.
Adam Brower wrote about his experience with one of them:
I can supply some perspective from my own experience. I noticed the
article today, too, and spent some time nodding my head and clucking
over my morning coffee.
For nearly a year, two years ago, I made it my personal mission to
convince just one bank to aggressively pursue just one phisher. I did
this, by the way, not as a representative of any anti-spam project, but as a
citizen. I encountered the expected silence from a majority of the
executives with whom I attempted to establish contact.
From a very few
others, I received polite thanks for my interest, advice to contact LEO,
and from two of them, invitations to open accounts!
After months of such wheel-spinning, a door seemed to open. I received a
thoughtful reply from a mid-level executive at a major New York-based
bank. We exchanged emails for three weeks. After he accepted my very
weak bona fides (I am, after all, far from expert in these matters, my
sole strengths being doggedness and an occasional way with language) I
sent him links to the wealth of investigative data available on the web,
samples of phishing spam targeting his institution, background info on
the rockphish phishing package
Et al., and he lapped it up. I was astounded that so much of
this was apparently news to a man in his position. We spoke on the phone
three times, each time ending with agreement that the bank's enormous
resources could and should be brought to bear against the crooks who were
victimizing its customers and costing it unreported millions in losses
each year. During the last call, he informed me that he intended to
whiteboard, at a coming meeting, the entire body of stuff I had sent
him, and to propose forming an internal task force to gather evidence
against the malefactors and to contact and interface with LEO. Naif that
I was, I was surprised when he hinted that there was institutional
reticence when it came to providing reports of compromises to LEO. It's
obvious to me now that the last thing in the world a big bank wants
announced is the scale of their losses in this context, or the number of
intrusions, but he seemed determined to stir the pot.
Subsequently, two weeks passed without a word. Email went unanswered.
One day I called the office number on which we had spoken earlier. I was
informed that Mr. Doe had left the firm. later, when I tried again, I
was told that no-one by that name had ever worked there. Whether our
conversations and his (supposed) departure were connected, who knows?
Maybe he just decided to take his golden parachute, but it certainly
could read like something from a Ludlum novel.
Stable link is https://jl.ly/Email/badbank.html
16 Aug 2009
Phishing is when bad guys try to impersonate a trusted organization,
so they can steal your credentials. Typically they'll send you a
fake e-mail that appears to be from a bank, with a link to a fake
website that also looks like the bank. Malware offers another
more insidious way to steal your credentials, by running unwanted
code on your computer that watches the keystrokes you type, the mouse
clicks you make, and the windows that appear on your screen, sends them
back to bad guy HQ, and even adds or substitutes its own keystrokes
and mouse clicks in a way that you can't easily detect.
I like Verisign's characterization of this kind of malware as an insecure
endpoint, the PC which is the endpoint of the conversation with the bank
isn't actually under the control of the person who's using it.
There's no question that straight phishes and malware are
different problems, but they attack the same customers toward the same
ends, and a lot of popular security strategies like those keyfob tokens
that generate a different random number every minute
are equally ineffective against both. There's also some overlap in
implementation, e.g. phishes that direct you to a website that downloads
malware.
We can usefully distiguish between offline and online attacks. An offline
attack steals credentials for use later, while an online attack sits
between you and the bank and does bad stuff in a session after you set
it up.
Offline attacks are deterred by changing the credentials from one session
to the next. The keyfob is one expensive way to do it, but there are
others. Most of my non-US bank accounts have two passwords where the
bank only
asks me for three randomly chosen letters of the second password each
time I log in.
I gather some European banks send their customers a printed list of
one-time passwords, and you use one and cross it out each time you log in.
None of these are effective against online attacks, since the bad guys
have a proxy that asks you the real questions from the bank and passes
back your real answers, setting up a real session
The problem is that there's an insecure endpoint,
either a malware infected PC on your desk, or the proxy which you think is
the bank and the bank thinks is you.
The solution either way is to switch to a secure endpoint. That's why I
have suggested a hardware USB confirmation dongle with a screen and
YES/NO buttons, where you set up the transaction on the insecure PC
but the dongle has an encrypted connection to the bank. so the
display on its screen and your push of the YES or NO button are secure.
Another possibility is a confirmation phone call to a phone which is physically
separate from your PC, where it reads you the transaction, and you press
1 for yes or 2 for no.
(Attention Users! Do not use a softphone on your PC for confirmations!)
It seems to me that although the details are different, the fundamental
problems and solutions are very similar, so it makes sense to consider
them together.
Stable link is https://jl.ly/Email/malphish.html
09 Aug 2009
In a discussion about a recent denial of service attack against Twitter,
someone asked
Some class of suppliers must be making money off of the weaknesses.
Anybody out there have a prescription for the cure?
Sure, but you're not going to like it.
See more ...
Stable link is https://jl.ly/cheap.html
04 Aug 2009
Last month the Ninth Circuit revived
CFIT's anti-trust case against Verisign.
On Thursday, Verisign filed
a most interesting
petition for rehearing.
See more ...
Stable link is https://jl.ly/ICANN/cfittrap.html
13 Jul 2009
Verisign makes a great deal of money from the .COM and .NET registries.
Can we tell how much they make, and how much that might change if
the CFIT lawsuit succeeds?
It's not hard to make some estimates from public information.
See more ...
Stable link is https://jl.ly/ICANN/vrsncom.html
04 Jul 2009
The DKIM standard has been out for two years now, and we're starting to
see some adoption by large mail systems, but there's still a lot of
misunderstanding about what DKIM does and doesn't do.
See more ...
Stable link is https://jl.ly/Email/threemyths.html
02 Jul 2009
Yesterday I said that the original
motivations for adding new TLDs were to break Verisign's monopoly on .COM,
and to use domain names as directories.
Competitive registrars broke the monopoly more effectively than any new domains,
and the new domains that tried to be directories have failed.
So what could a new TLD do?
See more ...
Stable link is https://jl.ly/ICANN/whoneeds2.html
01 Jul 2009
ICANN's Sydney meeting has come and gone, with the promised flood of
new top-level domains claimed to be ever closer to reality. Does the
world need more TLDs? Well, no.
See more ...
Stable link is https://jl.ly/ICANN/whoneedstlds.html
05 Jun 2009
Back in 2005 an organization called the Coalition for Internet Transparency
(CFIT) burst upon the scene at the Vancouver ICANN meeting,
and filed an anti-trust suit against Verisign for their monopoly control
of the .COM registry and of the market in expiring .COM domains.
They didn't do very well in the trial court, which granted Verisign's
motion to dismiss the case.
But yesterday the Ninth Circuit reversed the trial court and put the
suit back on track.
See more ...
Stable link is https://jl.ly/ICANN/cfit.html
Phishing, the theft of personal information by impersonating a trusted
organization, is a big problem that's not going away.
Most antiphishing techniques to date have attempted to recognize
fake e-mail and fake web sites, but this hasn't been particularly
effective.
A more promising approach is to brand the real mail and real web sites.
See more ...
Stable link is https://jl.ly/Email/phight.html
15 May 2009
![[A triskelion]](http://www.johnlevine.com/tris.png) I got a note from a college friend via Facebook yesterday, telling me
about the clever 282.im domain. Gee, it looked just like Facebook, like,
you know,
a
phish. Uh oh.
I got a note from a college friend via Facebook yesterday, telling me
about the clever 282.im domain. Gee, it looked just like Facebook, like,
you know,
a
phish. Uh oh.
See more ...
Stable link is https://jl.ly/ICANN/manx.html
06 May 2009
Viviane Redding, the Information Society
and Media Commissioner for the EC posted a
video
blog this week noting that the JPA between ICANN and the US Department
of Commerce ends this September.
In it she proposes that ICANN be overseen by a "G-12 for Internet
Governance" with 12 geographically balanced government representatives
from around the world.
That's such a non-starter that I'm baffled that she would even propose it.
See more ...
Stable link is https://jl.ly/ICANN/redding.html
24 Apr 2009
Press reports say that the Canadian government
introduced an anti-spam bill in the House of Commons today.
I haven't had a chance to read it yet, but since it's reportedly
based on the recommendations in the report from 2005 task force, of which I
was a member, signs are encouraging. I'll write more once
I've had a change to digest it.
Stable link is https://jl.ly/Email/c27a.html
31 Mar 2009
Last September the Virginia Supreme Court issued
a surprise ruling that reversed its previous
decision and threw out the state's anti-spam law on First
Amendment grounds.
The Commonwealth made a last ditch appeal to the US Supreme Court, which I
predicted they'd be unlikely to accept.
I guessed right, they
turned
it
down
yesterday, meaning the case is finally over.
Due to the peculiar facts and history of this case, the decision would be unlikely ever
to affect anyone other than Jaynes, and he's still in jail on other charges, so in the
big picture it's just a blip. I thought the VA legislature had already passed a
revised law that fixed the first amendment problem, but apparently not, since the
state Attorney General says
he's drafting a new law for next
year's session.
Even that's not all that important, since state laws are tightly constrained by CAN SPAM,
and can only make things that are already illegal under CAN SPAM more illegal.
The most useful difference a state law can make is to leave out the CAN SPAM language
about awarding costs which makes a losing CAN SPAM suit potentially very expensive
to the plaintiff.
Stable link is https://jl.ly/Email/jayneslast.html
17 Mar 2009
It's coming up on two years since the DKIM standard was published.
While we're seeing a certain amount of signed mail from Google,
Paypal, and ESPs, there's still a long way to go.
How hard is it to sign your mail with DKIM?
See more ...
Stable link is https://jl.ly/Email/dkimdepl.html
22 Feb 2009
Amazon recently released a new version of their popular Kindle e-book device.
One of the improvements is that it includes text-to-speech software that can
read an e-book aloud in a robotic voice.
The Authors Guild, the main trade association of book authors, immediately
claimed infringes the author's copyright, by making an
audiobook version of the book it's reading aloud.
That's ridiculous.
See more ...
Stable link is https://jl.ly/Copyright_Law/kindle2.html
04 Feb 2009
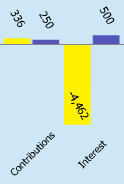 If you visit the new
dashboard
on ICANN's web site, you see some nice bar charts, including one rather large
negative number of $4,462,000.
If you click the little arrow at the top of the Financial Performance chart,
a footnote window pops open where the last sentence is:
If you visit the new
dashboard
on ICANN's web site, you see some nice bar charts, including one rather large
negative number of $4,462,000.
If you click the little arrow at the top of the Financial Performance chart,
a footnote window pops open where the last sentence is:
The large variance to budget is due to investment losses of $4.6 mil.
Investment losses? Yup, ICANN's been speculating in the stock market, and has
lost $4.6 million, or to put it in concrete terms, the 20 cent fee from 23 million
domain registrations.
See more ...
Stable link is https://jl.ly/ICANN/icannspec.html
24 Jan 2009
A friend asked:
Apparently the mortgage
holders today are not the loan originators and therefore have little
incentive to deal, or should I say workout, one-one with consumers. Can
[someone] provide some comments on workout
to help clarify
the concept?
Workouts are a normal part of bank lending, because
foreclosing (or the equivalent) is very expensive, and the bank is often
better off agreeing to a smaller or longer loan and actually getting paid.
See more ...
Stable link is https://jl.ly/Money/workout.html
02 Jan 2009
An acquaintance wondered why the people who run the systems that receive
mail get to make all the rules about what gets delivered.
After all, he noted:
The sender pays for bandwidth and agrees to abide by the
bandwidth provider's rules.
See more ...
Stable link is https://jl.ly/Email/whopays.html
|
Topics
My other sites
Who is this guy?
Airline ticket info
Taughannock Networks
Other blogs
CAUCE
It turns out you don’t need a license to hunt for spam.
34 days ago
A keen grasp of the obvious
Italian Apple Cake
592 days ago
Related sites
Coalition Against Unsolicited Commercial E-mail
Network Abuse Clearinghouse
My
Mastodon feed
|




![[A triskelion]](http://www.johnlevine.com/tris.png) I got a note from a college friend via Facebook yesterday, telling me
about the clever 282.im domain. Gee, it looked just like Facebook, like,
you know,
a
phish. Uh oh.
I got a note from a college friend via Facebook yesterday, telling me
about the clever 282.im domain. Gee, it looked just like Facebook, like,
you know,
a
phish. Uh oh.